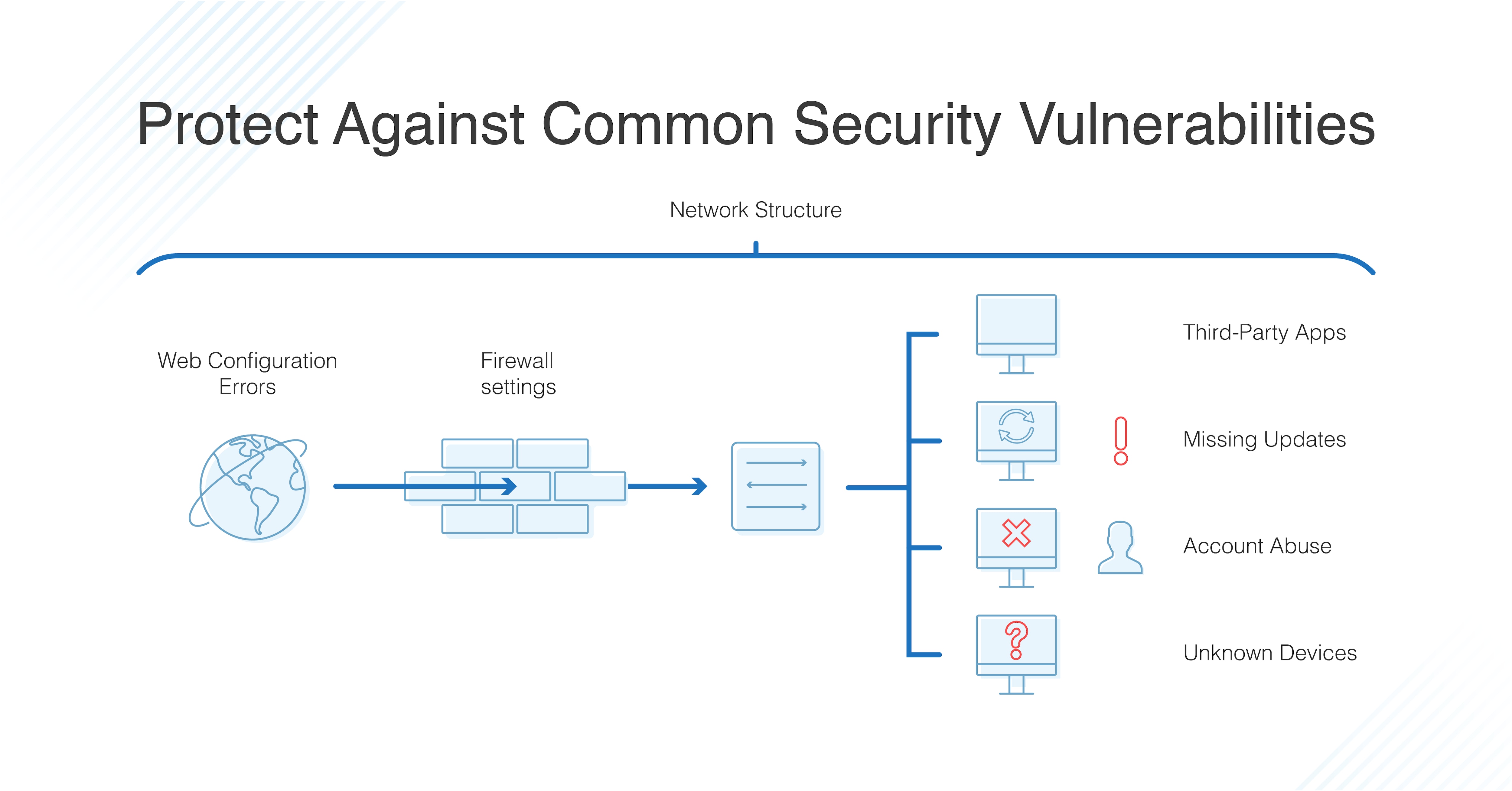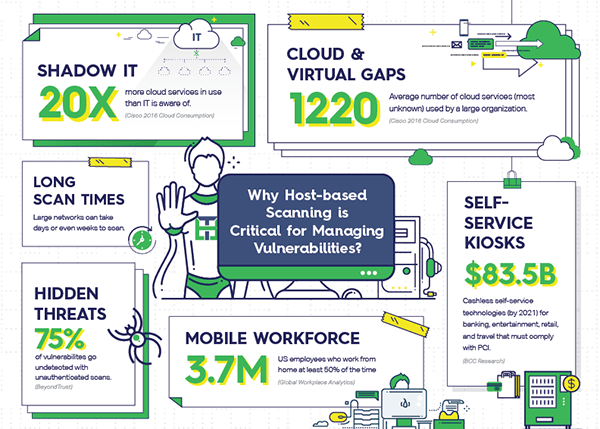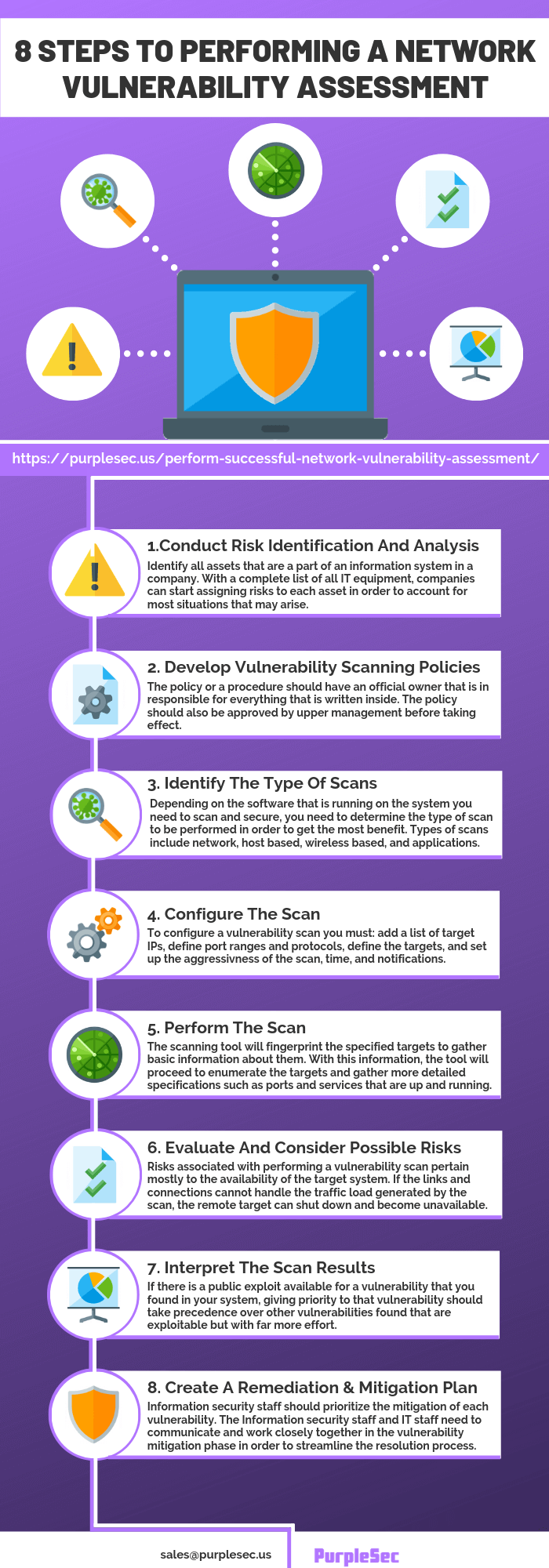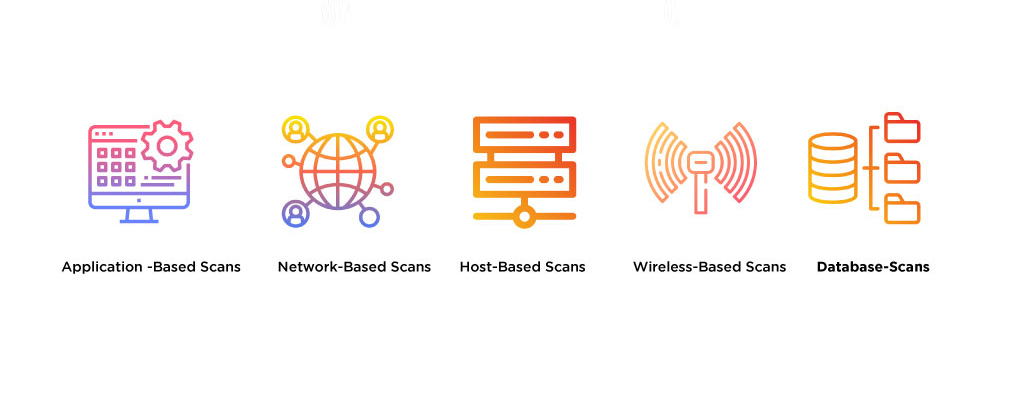
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus
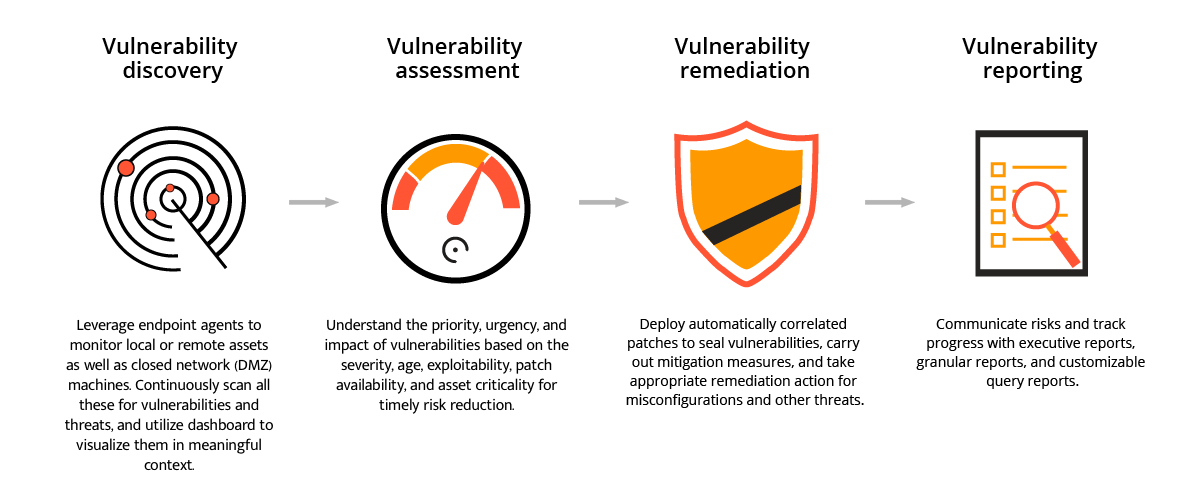
Vulnerability Scanner | Powerful Vulnerability Scanning Tools - ManageEngine Vulnerability Manager Plus

A host-based security assessment architecture for effective leveraging of shared knowledge | Semantic Scholar



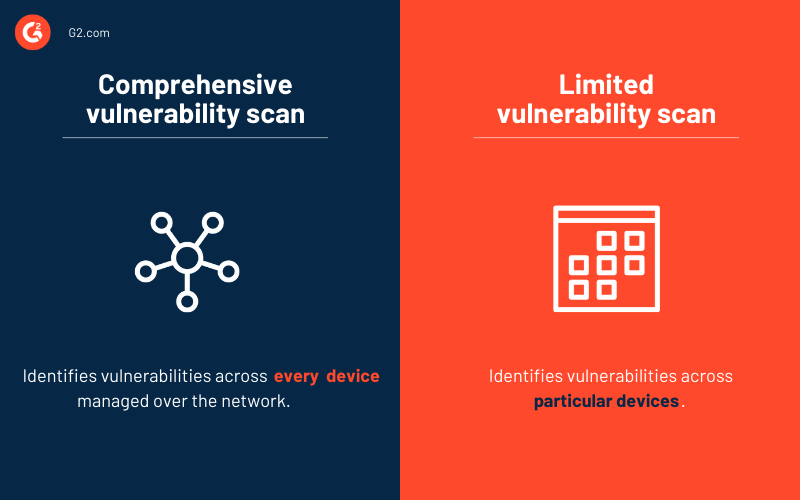
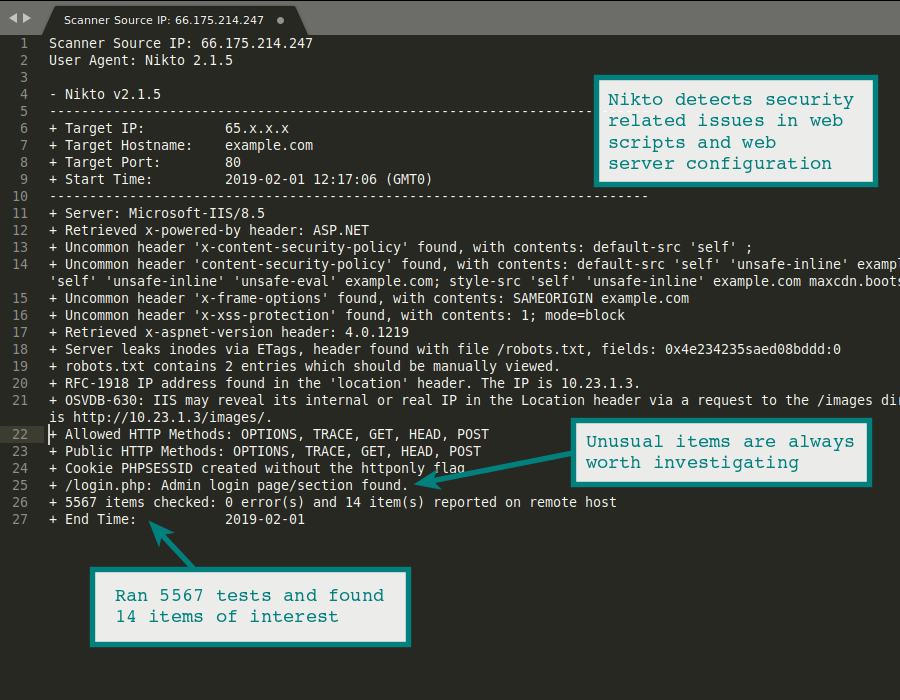
![Top 10 Vulnerability Scanners [Most Popular Scanners In 2023] Top 10 Vulnerability Scanners [Most Popular Scanners In 2023]](https://www.softwaretestinghelp.com/wp-content/qa/uploads/2021/09/Top-Vulnerability-Scanners-1.png)